Remote Access Scams: What You Need to Know to Stay Safe
In recent years, the number of remote access scams has massively increased. These scams involve fraudsters tricking individuals into granting them remotely access to their computers or mobile devices. they are now one of the biggest sources of ID theft. So what do you need to know to stay safe from remote access scams?
Let me break this down for you…
A scammer may impersonate a tech support agent, a service provider, or a government or law enforcement official.
They may also use various tactics, such as phishing emails, phone calls or SMS text messages to gain your trust. Remote access scams can have devastating consequences including financial loss, identity theft, and damage to your reputation.
Some scams are almost believable
Because scams impersonate popular brands and services and the circumstances copy real-life situations, they are almost believable. This is why they are so dangerous! Keep reading for simple ways for how you can avoid being scammed.
How Remote Access Scams Work
Remote access scams typically begin with a phone call or email from someone claiming to be a tech support agent or service provider.
They may claim that there is a problem with your computer or device and that they need remote access to fix it. They may also tell you that you are due to receive a refund from a recent online purchase or that a bill is overdue and your service will be suspended unless you make a payment immediately.
Alternatively, they may tell you that you’ve been the victim of a security breach and that they need to investigate the issue by gaining remote access to your device.
And this is where people run into trouble…
Once the scammer has gained remote access to your device, they can use it to install malware, steal sensitive information such as usernames, passwords, and financial data.
In some cases, they may also use your device to launch attacks on other systems or spread malware to your contacts.
Mostly, they use your computer or device to commit ID takeover. This is where they use your identity to sign up for services in your name and use your money to make payments or commit other crimes.

How to Protect Yourself from Remote Access Scams
To protect yourself from remote access scams, there are several steps you can take:
Be cautious:
Be careful if you receive an unsolicited phone call or email. Only provide personal information and only grant remote access to your device if you are absolutely sure that the person on the other end is legitimate.
Verify the identity of the caller or email sender:
If you need clarification on whether a caller or email sender is legitimate, ask for their name and contact information, and then verify their identity by contacting the company they claim to represent directly. Don’t use any contact information provided by the caller or email sender.
Red Flags to Watch Out For
Several red flags can indicate that a phone call or email is a remote access scam. Here are some of the most common ones:
1. Unsolicited contact: If you receive a phone call or email from someone you don’t know claiming to be a tech support agent or service provider, it’s essential to be cautious. Legitimate service providers typically don’t contact their customers unsolicited.
2. Urgency: Scammers may try to create a sense of urgency by telling you that your device has a serious problem that needs to be fixed immediately. They may also threaten to shut down your device or account if you don’t comply with their demands.
3. Request for remote access: If the caller or email asks for remote access to your device, it’s a major red flag. This is often a sign that they are trying to install malware or steal sensitive information.
4. Payment demands: Scammers may demand payment for their services or threaten to lock you out of your device unless you pay a ransom. Legitimate service providers typically operate differently.
5. Suspicious URLs or email addresses: Be wary of links or emails that look suspicious or unfamiliar. Scammers may use fake websites or email addresses to trick you into handing over sensitive information.
6. Bad spelling or grammar: Most scammers are based overseas so English is not their first language. Bad spelling or grammar in an email or SMS is an indicator of a potential scam.
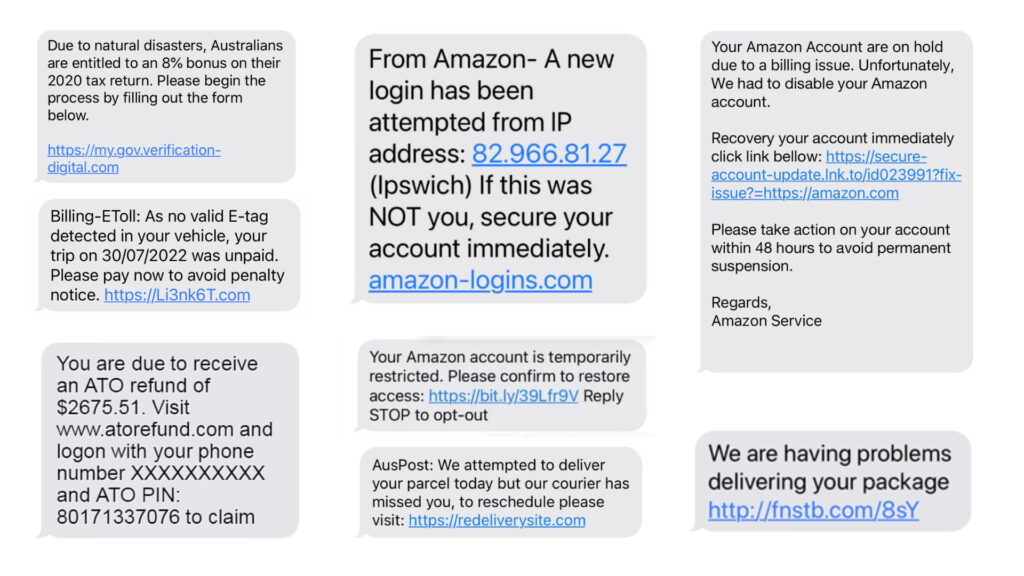
Remote Access Scams on Amazon
As one of the largest online retailers in the world, Amazon is a popular target for scammers.
How Remote Access Scams Work on Amazon
Remote access scams on Amazon typically start with an unsolicited phone call or email from someone claiming to be an Amazon representative or a member of the Amazon seller support team.
The scammer may argue that there is a problem with your Amazon account, such as an unauthorised purchase or a security breach.
They may also claim they need remote access to your computer or mobile device to fix the problem.
The problem is…
Once the scammer has gained remote access to your device, they can install malware or steal sensitive information such as your Amazon login credentials, credit card information, and other personal data.
They may also use your device to make unauthorised purchases on your Amazon account or launch attacks on other systems.
Install antivirus software:
Antivirus software can help protect your device from malware and other security threats. Be sure to keep your antivirus.
Methods scammers use to take remote access
AnyDesk is a popular remote desktop software that allows users to access and control other computers or mobile devices from a remote location. Unfortunately, scammers have also found ways to exploit the software to gain unauthorised access to other people’s devices. Here are some standard methods scammers use to take remote control of your computer or phone using AnyDesk:
Unsolicited Calls or Messages:
Scammers often reach out to people via unsolicited calls or messages, claiming to be technical support representatives or customer service agents.
They may ask you to install AnyDesk on your computer or mobile device to fix a technical issue. Once you install the software and provide them with the access code, they can take control of your device and steal sensitive information.
Fake Websites:
Scammers may create fake websites that look like the official AnyDesk website and trick you into downloading and installing a malware-infected software version.
This version of AnyDesk may give the scammers complete control of your device and allow them to steal your personal and financial information.
Social Engineering:
Scammers may also use social engineering techniques to trick you into giving them access to your device. For example, they may claim to be a friend or family member in trouble and ask you to install AnyDesk to help them out.
Alternatively, they may claim to be a government official or law enforcement agent and threaten legal action if you do not allow them to access your device.
Avoid remote access scams
To protect yourself from AnyDesk scammers, it’s essential to be cautious when downloading and installing software from the internet.
Only download software from trusted sources, such as the official AnyDesk website, and never give out your access code to anyone you don’t know or trust.
Additionally, always be sceptical of unsolicited calls or messages and verify the identity of the person or organisation before giving them access to your device.
Better still, NEVER download remote access software ever! If you are unsure and need help with a device problem, we suggest you physically go to a reputable and trusted local service centre for help.
About Rocket Remit
Rocket Remit is the worlds fastest international money transfer service. Send money instantly to over 50 overseas countries at very competitive rates.
Use the country selector to choose the country and check the rate.
Click here for more information on how to send money using Rocket Remit.